Sophos Rapid Response stresses the importance of monitoring account credentials in every organization. This 24/7 service helps businesses quickly detect and stop ransomware attacks.
One company contacted Rapid Response for help with a Nefilim (Nemty) ransomware attack. The attack had already impacted more than 100 systems. Sophos’ Intercept X endpoint protection can detect and block Nefilim easily. Unfortunately, the company did not have this protection installed.
Nefilim ransomware encrypts original files, replacing them with locked versions. Recovery is impossible without a decryption key or recent backup.
The Rapid Response team acted immediately after being contracted. They installed Sophos security on all accessible systems, enabled protections on machines with existing Sophos tools, and searched for evidence of the attack’s origin and stolen data.
By the time they held their standard “kick-off” call, the team had already identified compromised user accounts and created a timeline of the attack.
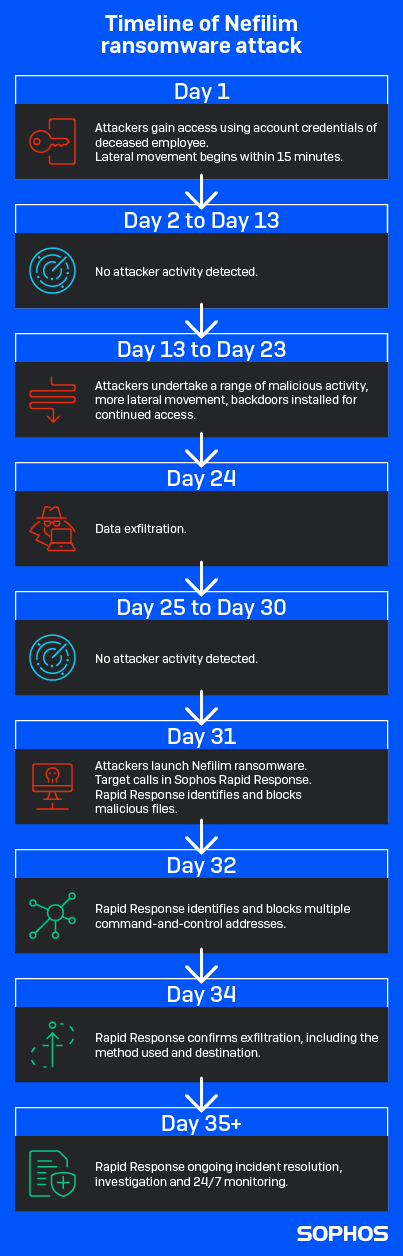
The team found that the attacker had compromised an admin account with high-level access a month before deploying Nefilim ransomware. They gained access to this account, then spent weeks moving through the network. During that time, they stole credentials for a domain admin account, identified valuable data, exfiltrated hundreds of gigabytes, and finally launched the ransomware.
“Ransomware is the final payload in a longer attack,” said Peter Mackenzie, Rapid Response Manager. “It means the attacker already controls your network and has completed the real damage. Detecting ransomware is easy—catching the attacker before they strike is what matters.”
Sophos intelligence showed that Nefilim attackers often exploit Citrix or Remote Desktop Protocol (RDP) for initial access. In this case, they exploited vulnerable Citrix software. Using Mimikatz, they stole credentials for a domain admin account.
During the initial call with the customer, the Rapid Response team revealed the compromised admin account. Shockingly, it belonged to an employee who had died three months earlier. The account remained active for services, forcing the team to separate legitimate activity from malicious actions.
“The attacker operated mostly at night in the customer’s local time,” Mackenzie said. “This helped us trace which actions were genuine and which were not.”
He advised companies to disable accounts that are no longer needed. If an account must remain active, convert it to a service account and block interactive logins. Organizations should also audit Active Directory regularly. Audit policies can track admin activity or detect when new accounts join the domain admin group.
Mackenzie emphasized that few people truly need domain admin access.
“Executives or IT leads don’t need full-time domain admin accounts,” he said. “Use privileged accounts only when necessary, and monitor their use closely.”
He also recommended setting alerts for any use of domain admin accounts or creation of new ones. A previous Rapid Response case showed why this is critical.
In that case, an attacker gained access to a network, created a new user, and added it to the domain admin group. No alerts were triggered. The attacker then deleted 150 virtual servers and encrypted backups with BitLocker.
“They were lucky the attack was so loud,” Mackenzie said. “If it had been stealthy, the attacker could have held domain admin access for months without detection.”
Detection and IoCs
Sophos Endpoint Protection detects Nefilim as Troj/Ransom-GDN. Additional IoCs are available on SophosLabs GitHub.
Nefilim Tactics, Techniques, and Procedures (TTPs)
-
Exploit public-facing applications like Citrix (MITRE ATT&CK T1190)
-
Use RDP for persistent access
-
Deploy tools like Mimikatz to steal credentials
-
Move laterally using PowerShell, RDP, and Cobalt Strike
-
Exfiltrate data using MEGA
-
Deploy ransomware via Windows Management Instrumentation (WMI)
Checklist for Secure Account Access
-
Grant only necessary permissions
-
Disable unused accounts
-
Convert active-but-unmanned accounts into service accounts with no interactive login
-
Audit Active Directory regularly and monitor for privilege changes
-
Use advanced anti-ransomware solutions like Sophos Intercept X